

70 percent of modern cyber threats are now identity-related, with attackers choosing to log in with stolen credentials rather than break in.
Raluca Saceanu, Group CEO of Smarttech247, explains that this trend is the reason popular defenses like Zero Trust are struggling and why the concept of a human firewall is a flawed strategy.
Saceanu cautions against fully autonomous security, proposing instead an AI-enabled model that amplifies human expertise to create a more resilient defense against sophisticated social engineering.
The primary perimeter of modern cybersecurity is moving from the network to human identity. Instead of leveraging sophisticated malware or deploying complex code, attackers are mastering the art of social engineering to simply log in, and they're getting faster.
Raluca Saceanu, Group Chief Executive Officer of Smarttech247, says this type of attack isn't new, but it is underestimated. Recognized as one of the Top 100 Women in Tech for 2025, Saceanu has built her career on the front lines of threat detection and response. Her work offers a direct look at how adversaries are exploiting our most trusted systems and why conventional defenses are often challenged.
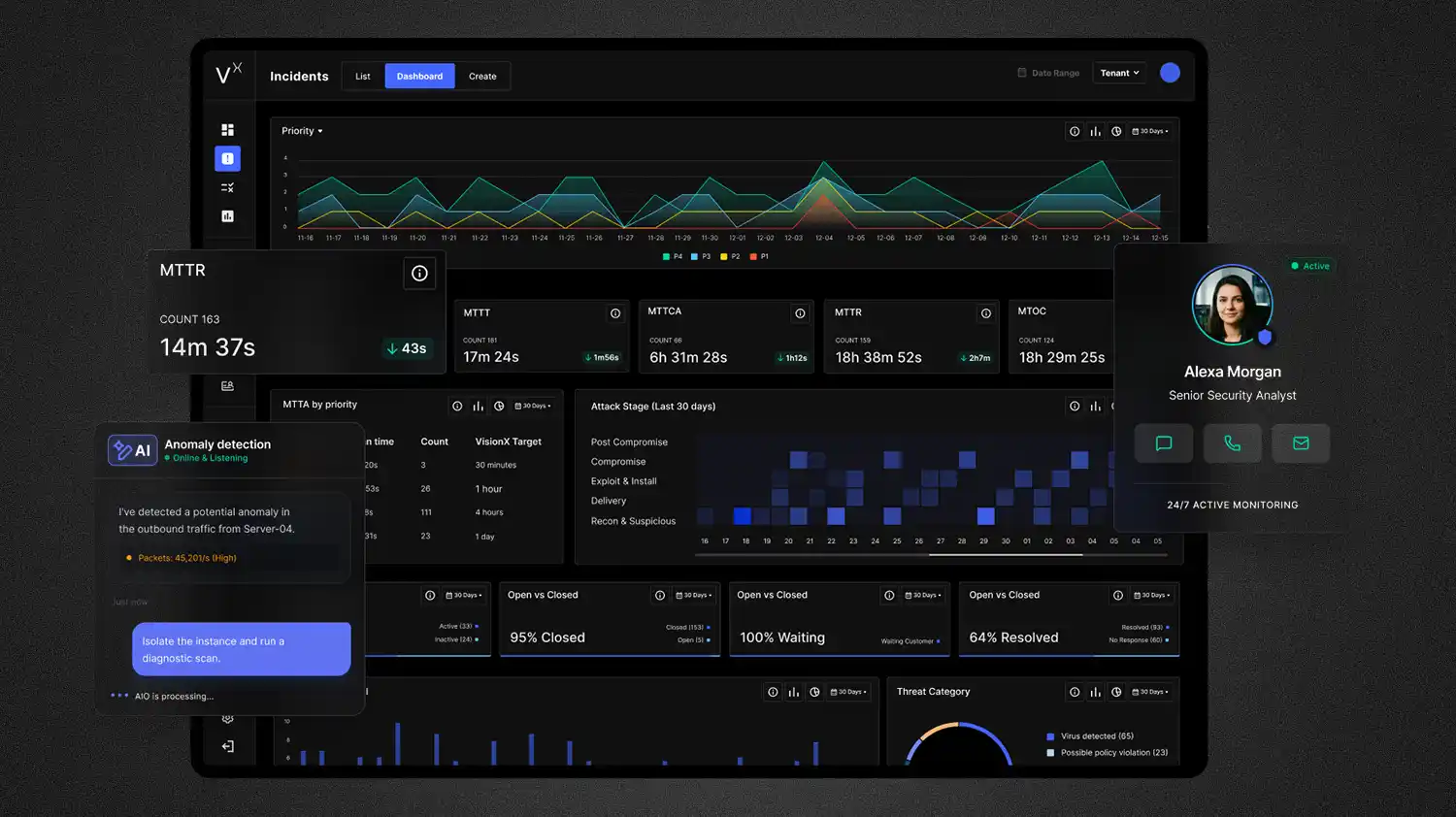
“Identity is now at the core of everything from an attack surface perspective. Nearly 70 percent of the threats we’re investigating are identity-related threats,” Saceanu says. It's a significant evolution in the modern attack lifecycle from breaking in to logging in. "There's a huge misconception in this industry that attacks are super sophisticated, but that's not actually true. The basics are still really important."
Anyone can be a target: Adversaries increasingly rely on user-driven social engineering techniques to gain initial access, ranging from phishing and MFA fatigue to more recent approaches like ClickFix, before moving laterally and quietly through the environment. "Attackers aren’t going straight for administrators," Saceanu says. "They’re targeting any user who gives them access. A marketing executive falls for a phishing lure, and suddenly the attacker is inside the network, operating as a legitimate employee and blending into normal activity."
Hiding in plain sight: "Once attackers get inside, they begin probing the environment and moving laterally," she explains. "Much of that activity can closely resemble normal user behavior, even in well-controlled environments." Campaigns that once unfolded over hours or days can now escalate in minutes, outpacing security models that rely heavily on static rules or lack behaviral context. Because of this, intrusions can go undetected long enough for attackers to establish persistence or prepare data extortion.
The detection challenge comes from a tactic called living off the land where attackers abuse legitimate, pre-installed tools like PowerShell. Since the tools are native to the platform, the activity doesn't trigger alerts like traditional malware would. These attacks disproportionately target industries like manufacturing and healthcare, whose intolerance for operational interruptions makes them prime targets. "They can't have any operational disruption and they're the first ones to pay," Saceanu says. Plus, there's another financial incentive, since credentials can sell for tens of thousands of dollars.
The personal touch: "Even as a cybersecurity company, we face the same phishing and social engineering threats as everyone else," Saceanu says. “For us, the number one risk is CEO impersonation." She explains how malicious actors craft highly convincing attacks by using platforms like LinkedIn for intelligence gathering. "Attackers will try to impersonate me and go after my new employees, specifically the people they've identified on LinkedIn who have just started with the company."
According to Saceanu, this new reality helps explain why popular frameworks like Zero Trust are failing in the wild and why a fully autonomous SOC is an unworkable concept. While attackers leverage AI for phishing, the defense cannot be fully automated. She noted that this same problem of trust will likely be amplified by the next wave of technology.
An identity crisis: "The fundamental issue isn’t Zero Trust itself, but how identity has traditionally been treated," Saceanu says. "Identity programs have often been designed and owned as IT initiatives, focused on access and lifecycle management, rather than as core security controls. As a result, organizations have built strong access frameworks without equal emphasis on detecting when identity is being abused."
Humans vs. humans: Saceanu likens automated security defenses to autonomous cars, noting that a core limitation of both technologies is their difficulty in handling unpredictable, adversarial human behavior. "You can’t design an automated system that reliably anticipates the intent and decision-making of other human actors in every scenario," she says. "That’s why security can’t be fully autonomous. At the end of the day, you’re still defending against a human adversary who adapts in real time."
Saceanu’s solution is an AI-enabled model that amplifies human expertise rather than replacing it. Her approach uses automation for repeatable, high-volume tasks such as SIEM alert triage, allowing experienced analysts to focus on judgement-driven decisions. It also relies on adaptive controls, such as conditional access policies that enforce phishing-resistant MFA when abnormal behavior is detected, so security responses evolve dynamically as risk changes.
The magic formula: The future Saceanu envisions is an AI-enabled setup where human judgement is amplified by the speed and scale of automation. "We shouldn’t be spending time on the grunt work. We should be spending time on the important stuff," she says. In practice, that means using automation to correlate signals, suppress noise, and surface high-confidence incidents, while human analysts take ownership of investigation and response. "Depending on the complexity of the environment and the incident, you still need a senior analysts to apply context, assess risk, and make the final call. To me, that’s really the magic formula."
Successfully combatting these threats often means leaders must elevate their view of security, treating it as a core business function with a direct impact on operational resilience. "You have to take cybersecurity as seriously as you take a profit and loss statement," Saceanu insists. "Your resilience and your mentality around operational disruption will be a huge part of how you respond to an incident."
Finally, Saceanu challenges one of the industry's most common refrains, which is the concept of the human firewall. She notes that today's attacks are so sophisticated that even cybersecurity professionals fall victim to them. "You can't ask a hospital nurse, who is already stressed enough, to tell the difference between a sophisticated phishing attack and a real email. That's not their job," she says. "Stop thinking about your employees as the frontline of defense, because they are not. You need to build good walls, good protection, so that if someone does get phished, you can stop it there."